Objectives
To establish a Virtual Private Network (VPN) between a local PFSense firewall (company-A) and a remote PFSense firewall (company B) with a built-in feature called OpenVPN.
Prerequisites
- companyA.localdomain (Local/Client) – https://192.168.13.152/ (WAN Interface)
- companyB.localdomain (Remote/Server) – https://192.168.13.175/ (WAN interface)
- Hypervisor of choice (Promox VE/VirtualBox)
- PFSense V2.4.3 – https://www.pfsense.org/download/
NOTE: If you have IPSec configured before proceeding to OpenVPN, please ensure the IPSec connection is disabled.
Steps
Task 1: Remote/Server side configurations
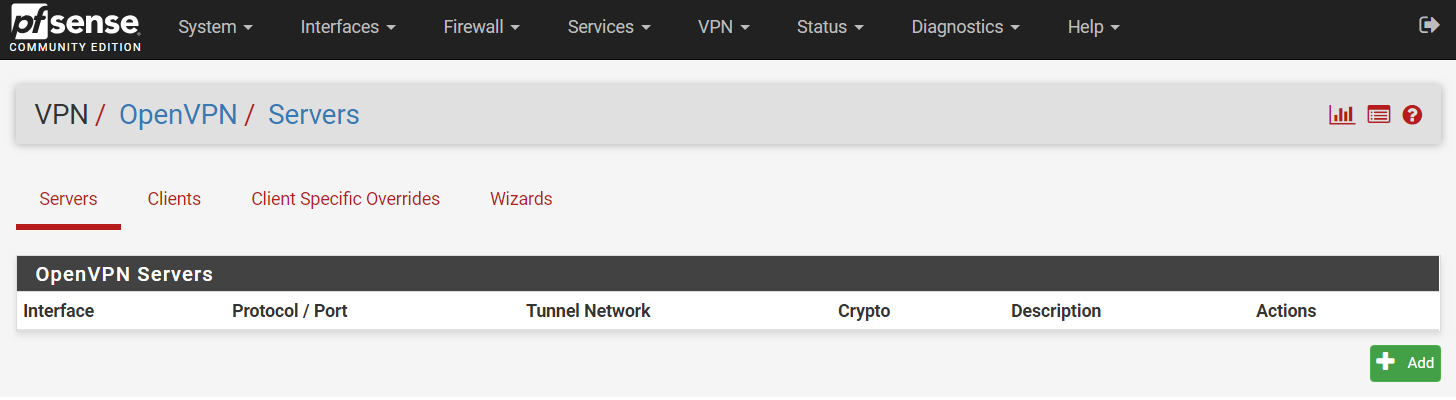
Step 1: Access your PfSense firewall (Company B) via the IP address stated above, go to VPN > OpenVPN > Servers.
Step 2: Click ‘+ Add’ button.
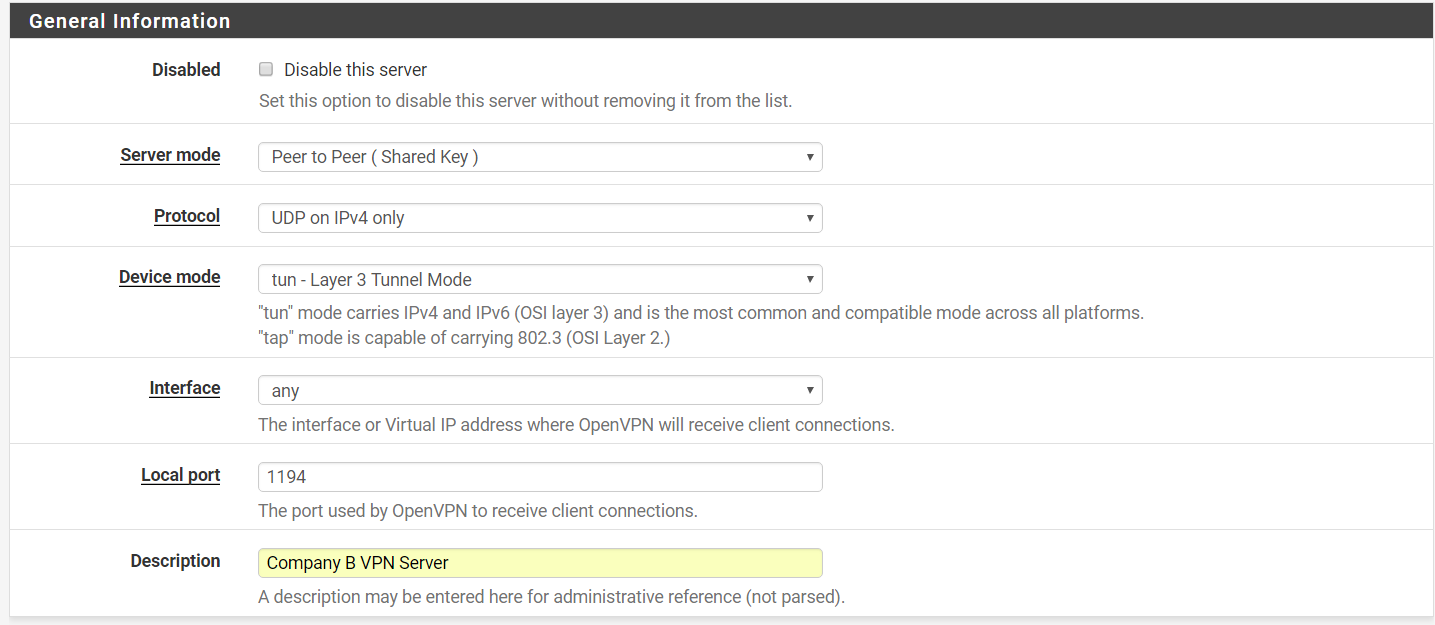
Step 3: Under General Settings: –
Server Mode > Peer-to-peer (Shared Key)
Protocol > UDP on IPv4 only
Device mode > Layer 3 Tunnel Mode
Interface > any
Local Port > 1194 (auto-assigned)
Description > Company B VPN Server
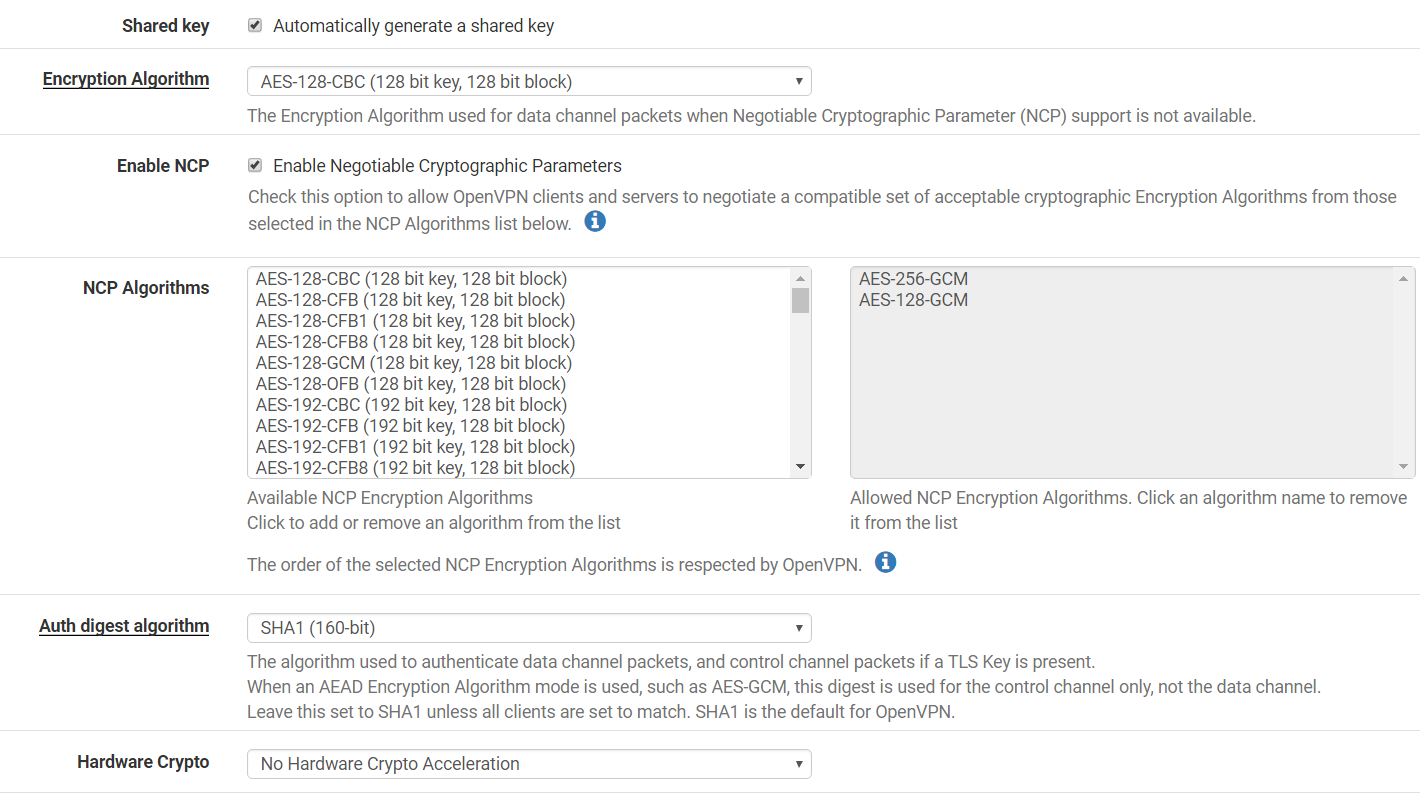
Step 4: Under Cryptographic Settings:-
Shared Key > Checked
Encryption Algo > AES-128-CBC
Enable NCP > Checked
NCP Algorithms > Default list
Auth digest algo > SHA1 (160-bit)
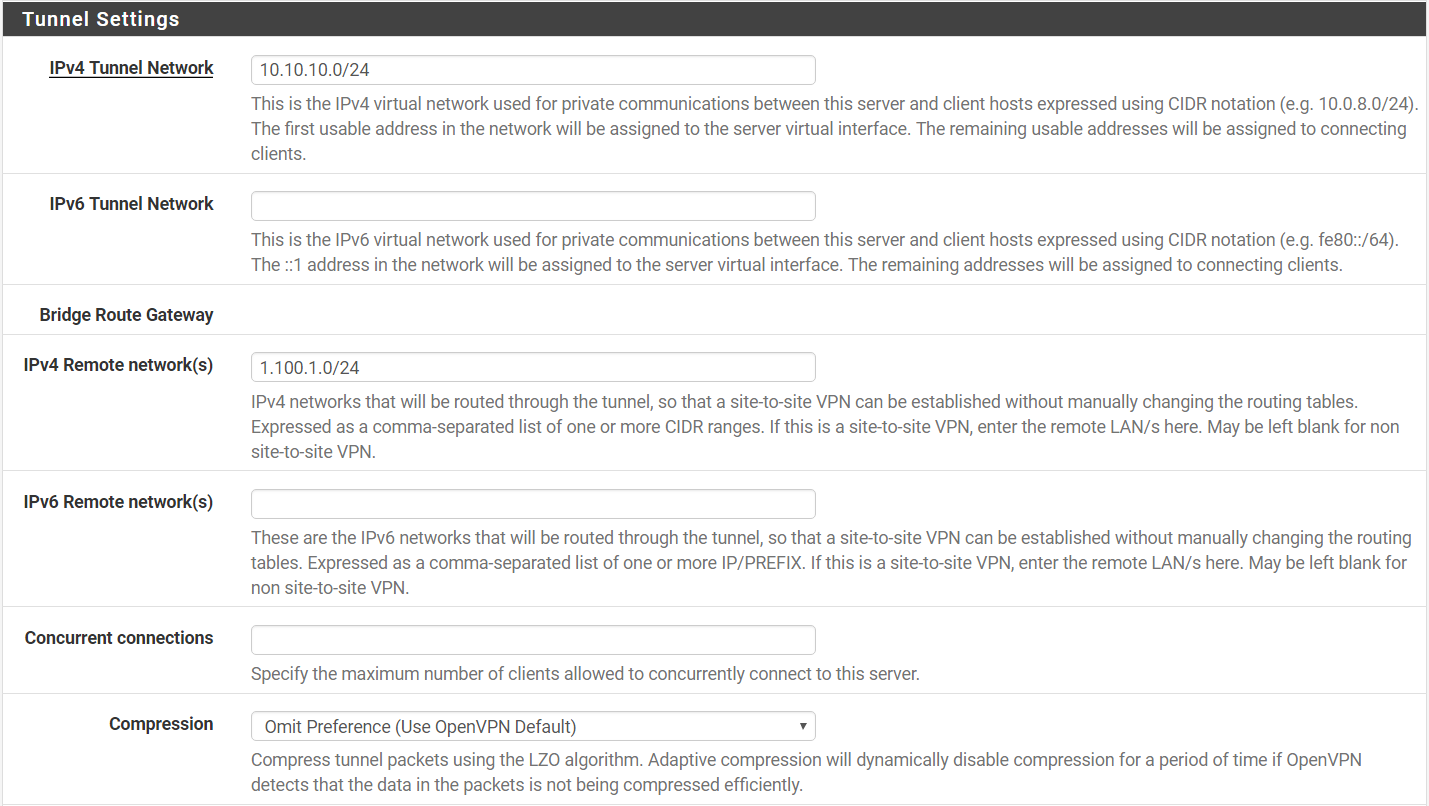
Step 5: Under Tunnel Settings:-
IPv4 Tunnel Network > 10.10.10.0/24
IPv4 Remote Network > 1.100.1.0/24
Compression > Omit Preference (Use OpenVPN Default)
Step 6: Ignore the settings under Advanced Configurations
Step 7: Save your settings (Bottom of the page). An entry of the created OpenVPN server will be added.
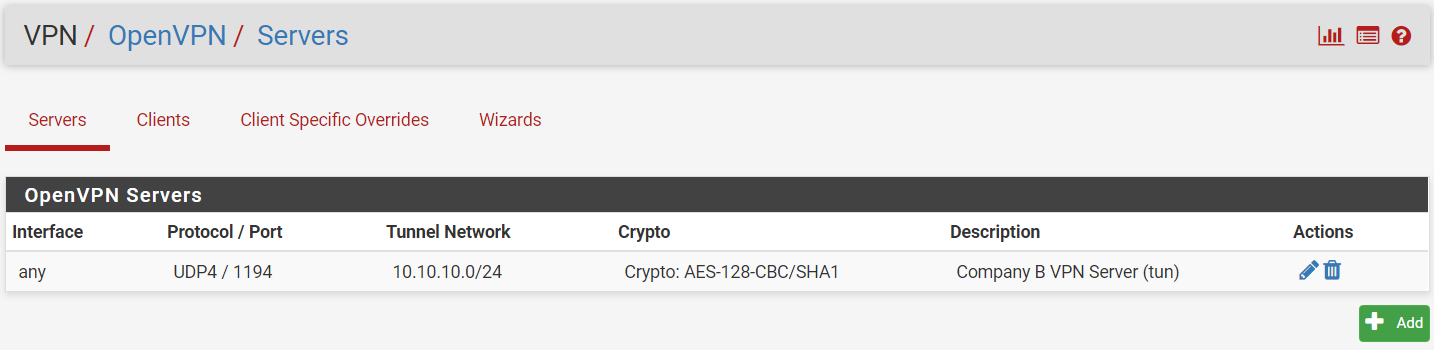
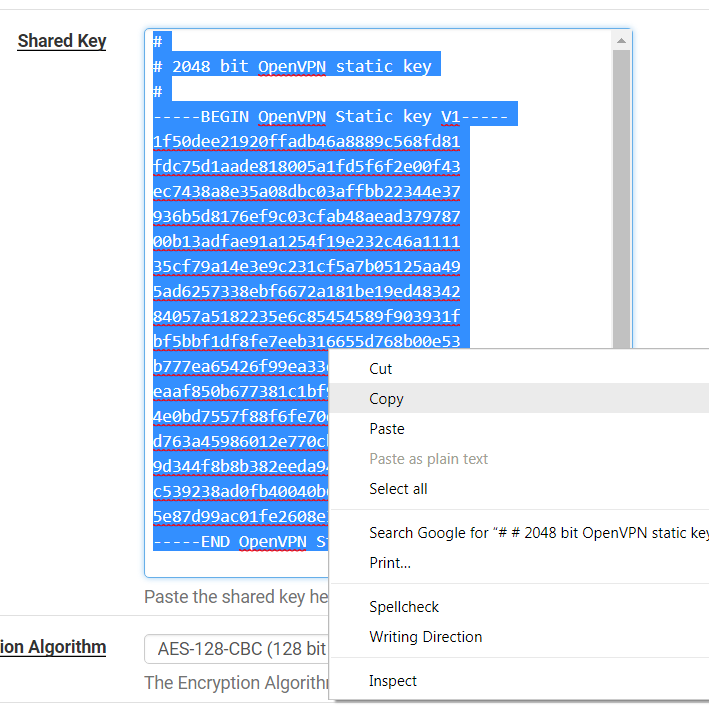
Step 8: Return to your settings by clicking on the pencil icon and copy the generated shared key.
Task 2: Local/Client side configurations
Step 1: On your PFSense firewall (Company A), go to VPN > OpenVPN > Clients.
Step 2: Click ‘+ Add’ button.
Step 3: Under General Settings: –
Server mode > Peer-to-peer (Shared Key)
Protocol > UDP on IPv4 only
Device mode > Layer 3 Tunnel Mode
Interface > any
Local Port > leave empty
Server host or address > 192.168.13.175
Server port > 1194
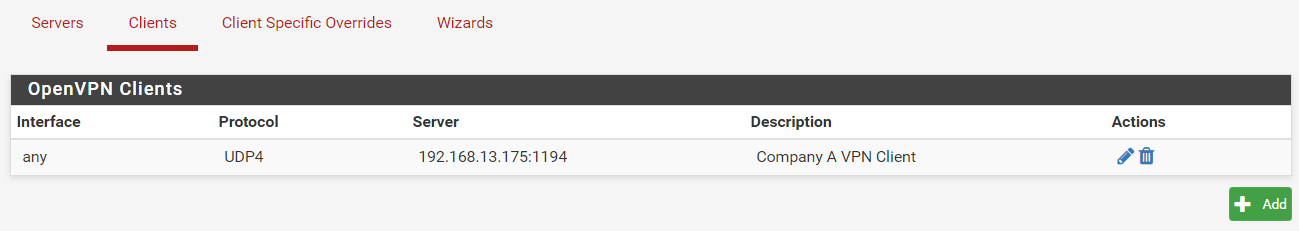
Description > Company A VPN Client
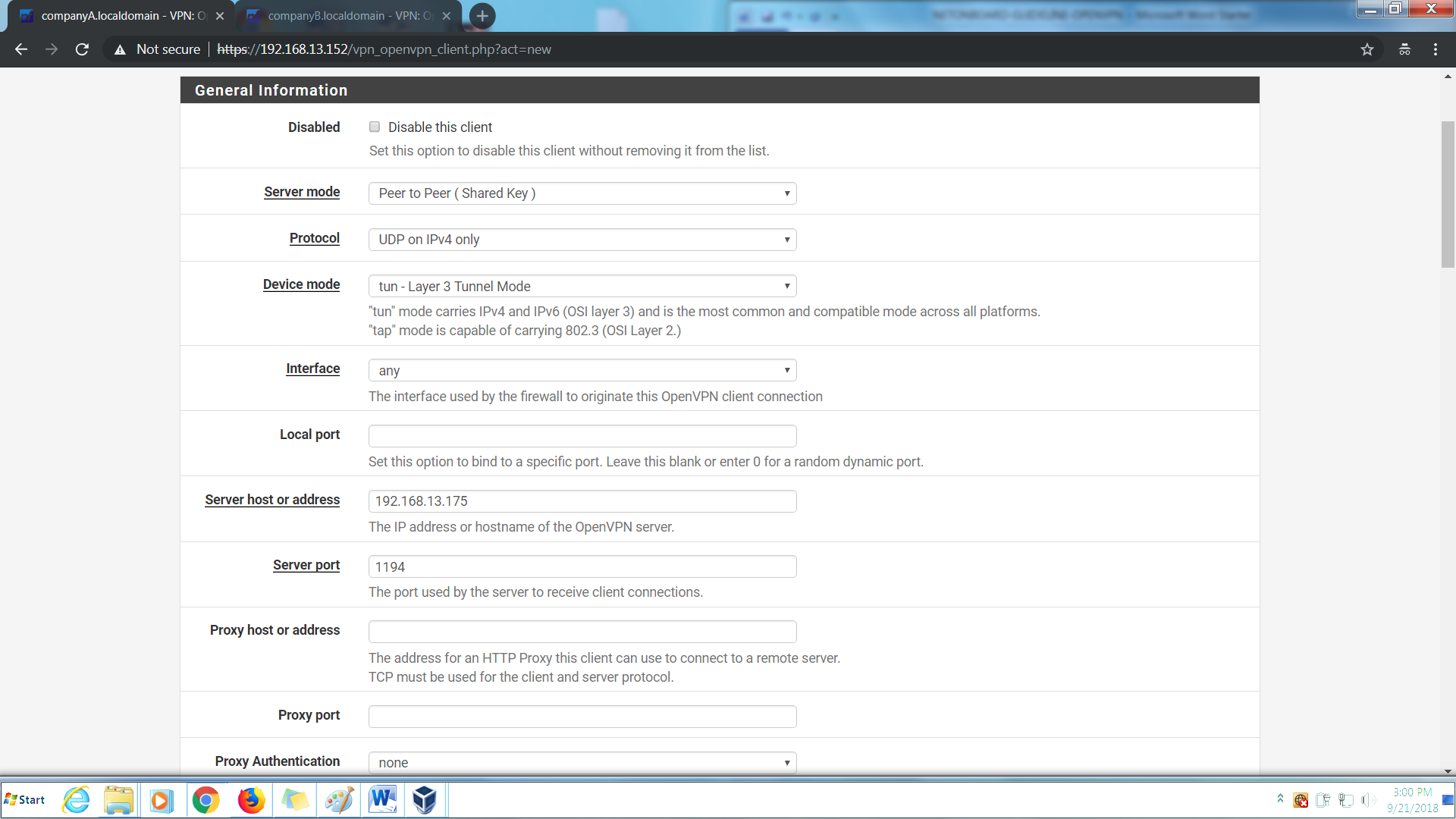
Step 4: Under Cryptographic Settings:-
Auto generate > Unchecked
Shared Key > Paste the key (Obtained from server side)
Encryption Algorithm > AES-128-CBC
Enable NCP > Checked
NCP Algo > Default List
Auth digest algorithm > SHA1 (160-bit)
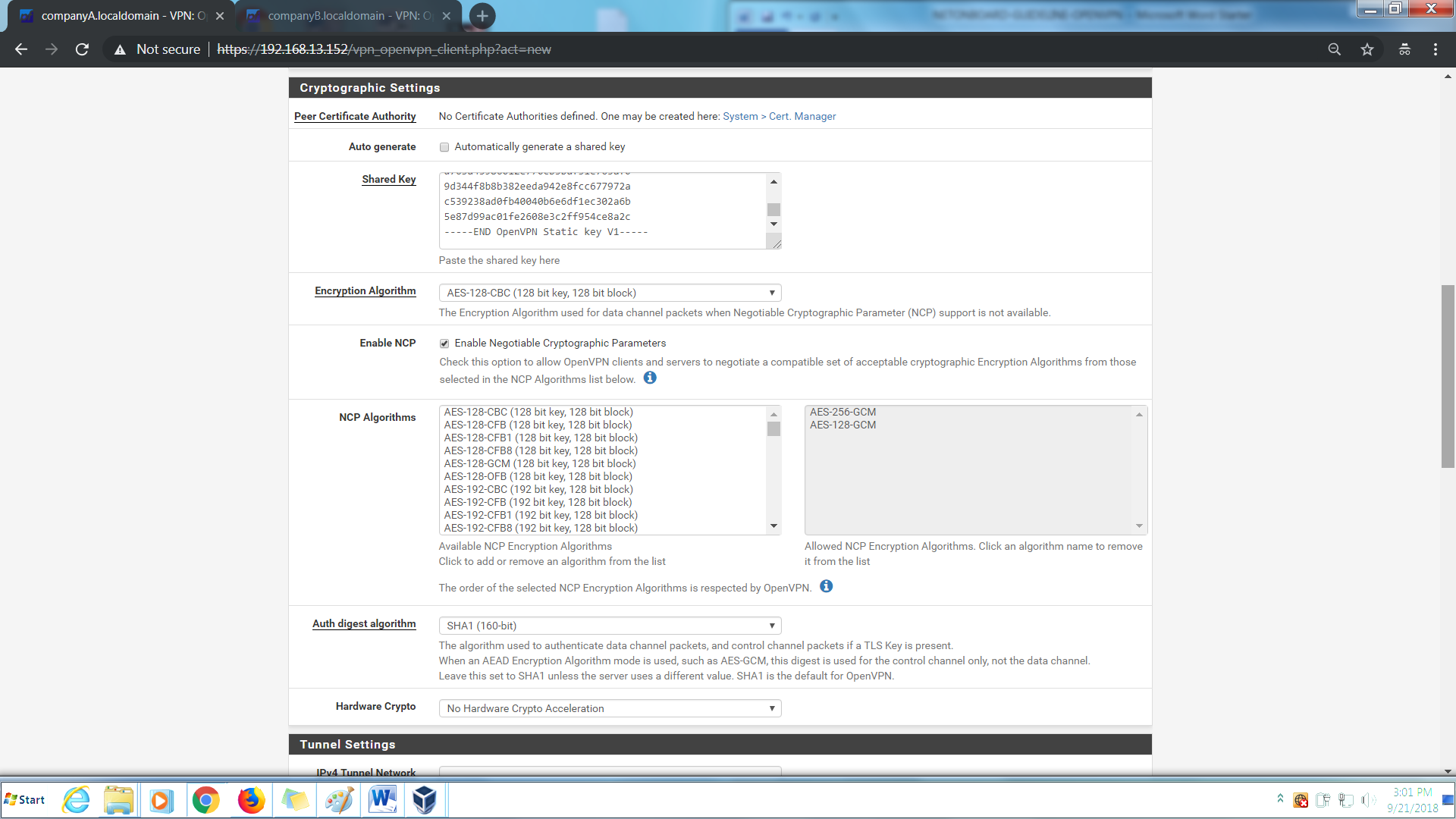
Step 5: Under Tunnel Network:-
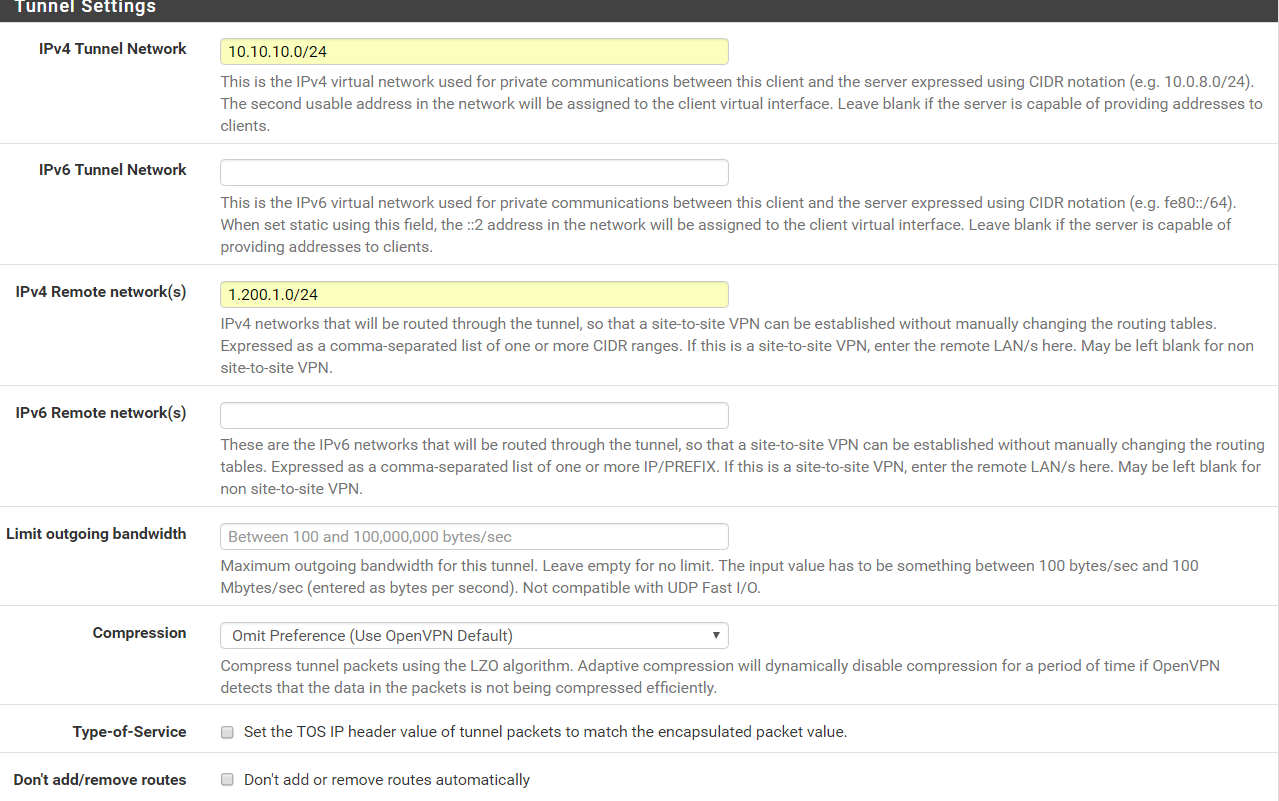
IPv4 Tunnel Network > 10.10.10.0/24
IPv4 Remote Network > 1.200.1.0/24
Compression > Omit Preference (use OpenVPN Default)
Step 6: Ignore the settings under Advanced Configurations and save. An entry of the created VPN Client will be added.
Task 3: Adding Firewall Rules
Step 1: On the PfSense firewall (Company B), go to Firewall > Rules > WAN
Step 2: Add the following rule:-
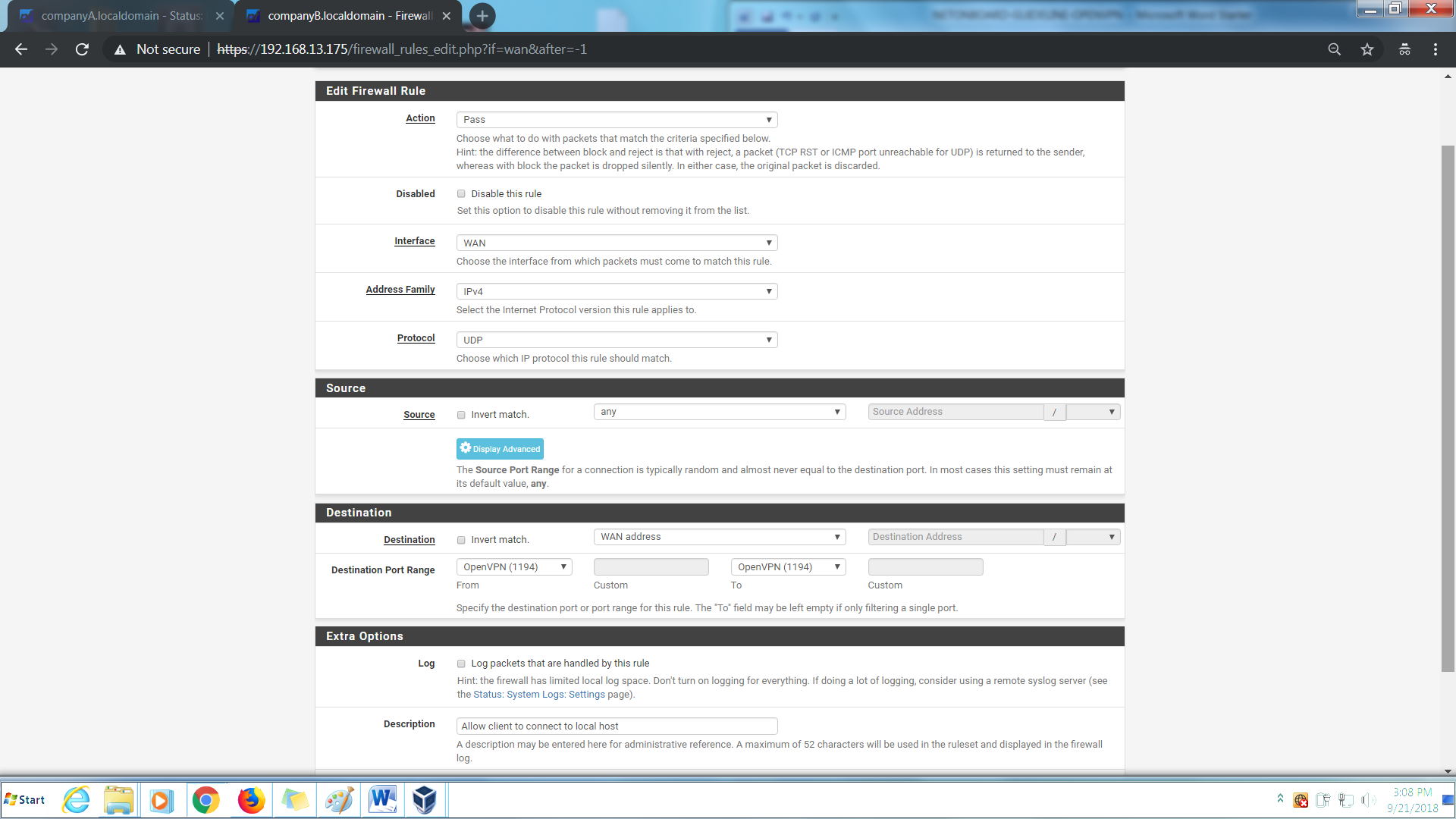
1st Rule
Action > Pass
Protocol > UDP
Source > any
Destination > WAN Address
Destination Port Range > OpenVPN (11XX)
Description > Allow client to connect to local host
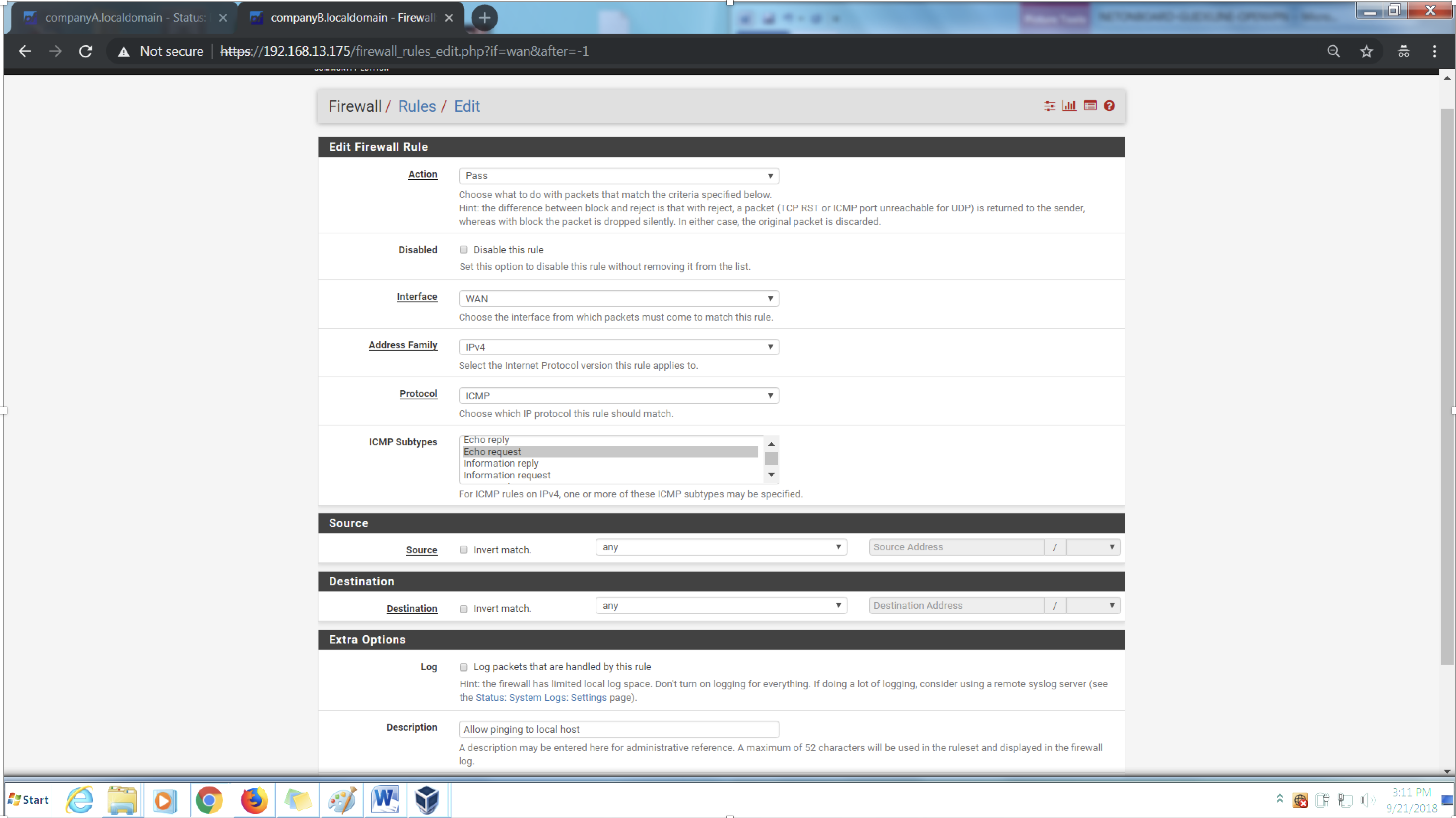
2nd Rule
Action > Pass
Protocol > ICMP
Subtypes > Echo request
Source > any
Destination > any
Description > Allow pinging to local host
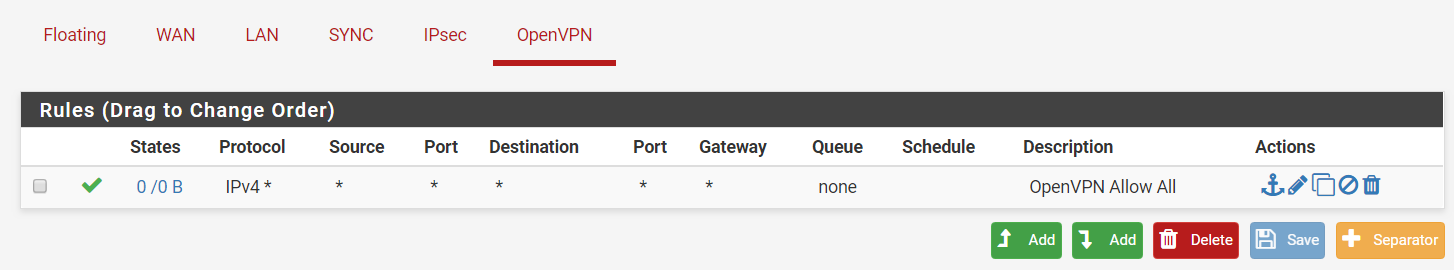
Step 3: Next, on your OpenVPN interface, add the following rule:-
Action > Pass
Protocol > any
Source > any
Destination > any
Description > OpenVPN Allow All
Step 4: On the PFSense firewall (Company A), go to Firewall > Rules > OpenVPN
Step 5: Add the following rule:-
Action > Pass
Protocol > any
Source > any
Destination > any
Description > OpenVPN Allow All

Task 4: Verification Tests
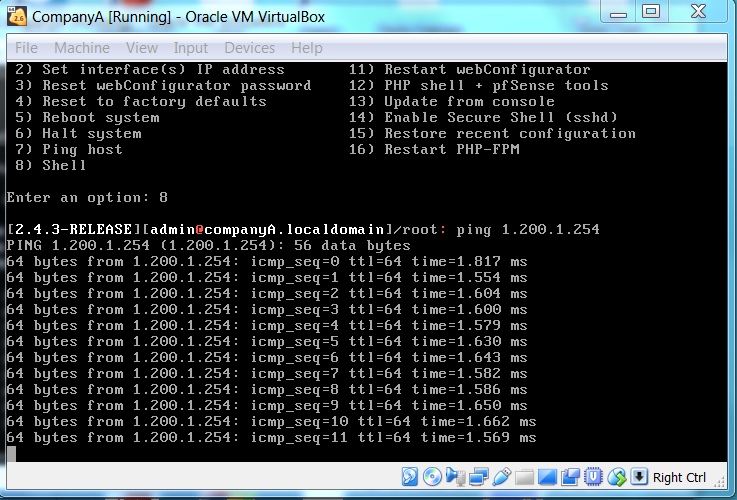
Step 1: Perform a ping test from local firewall (Company A) to the remote firewall (Company B) to ensure the connection has been established. This can be done either through console or the firewall itself (Diagnostics > Ping).
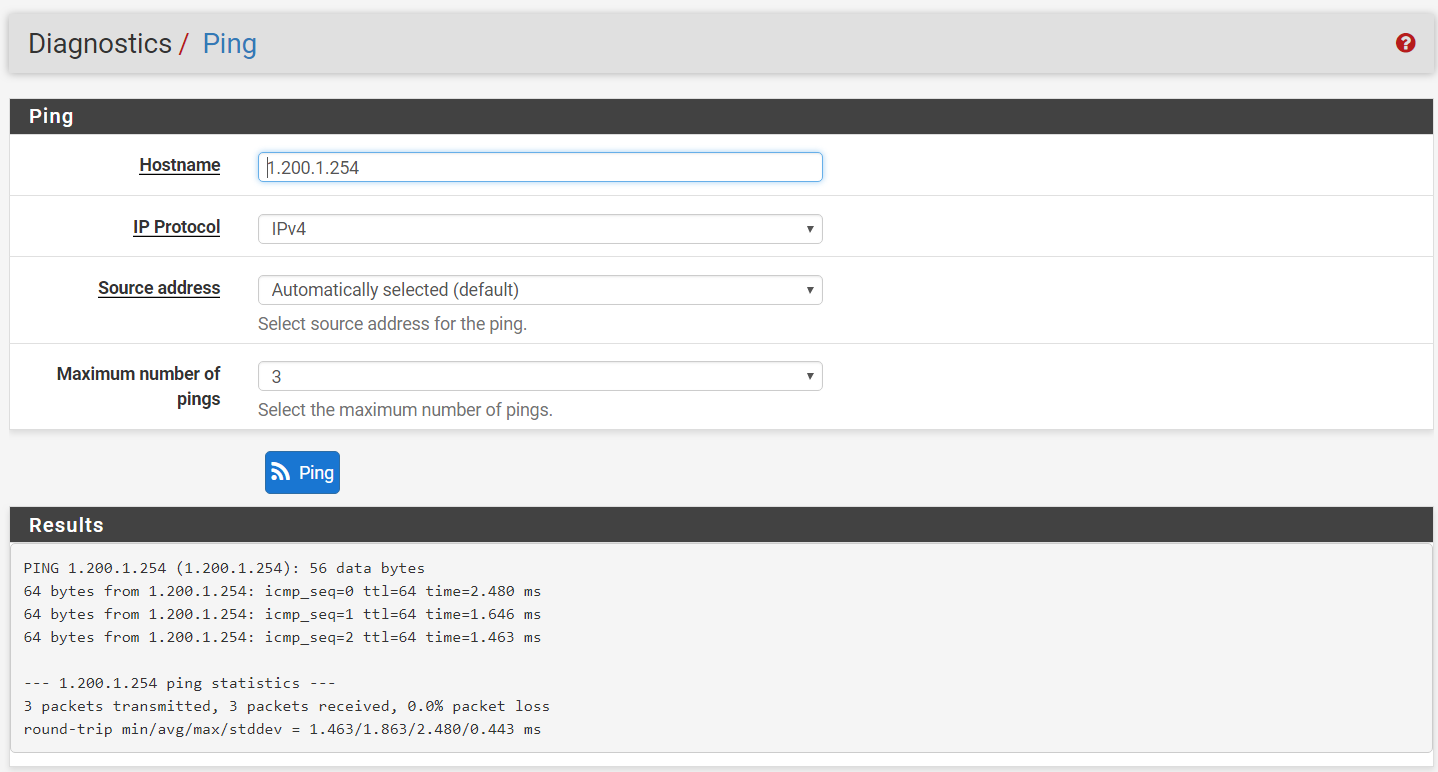
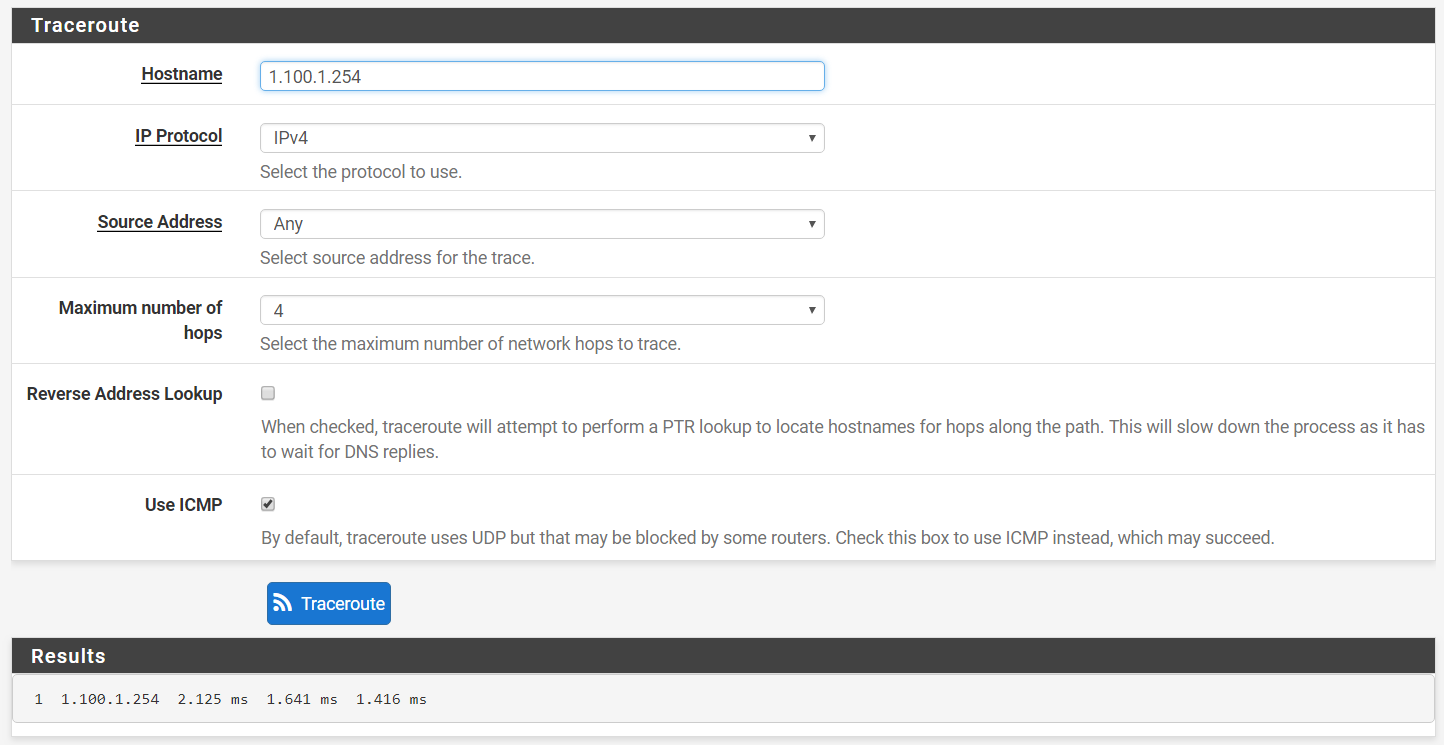
Step 2: Perform a traceroute from remote firewall (Company B) to local firewall (Company A), the result should show only one hop to the destination (Diagnostics > Traceroute).
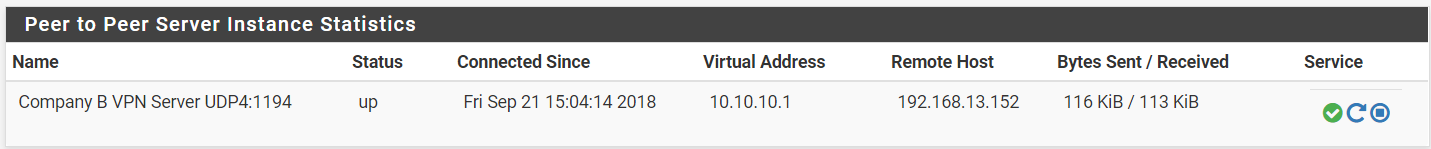
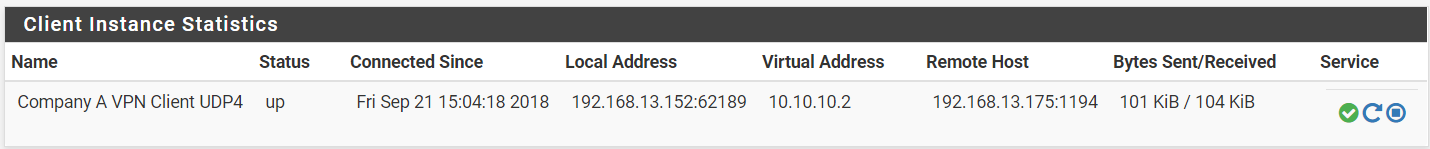
Step 3: Ensure the OpenVPN connection currently running by navigating to Status > OpenVPN.
Company A (Client):
Company B (Server):